Why should organizations conduct a data inventory?
Although a data inventory is not required, you do need a record of processing activities (ROPA). It’s difficult to meet GDPR Article 30 compliance without a data inventory and map to visually represent how data flows throughout your organization.
A data inventory process focuses on how and why data is collected to ensure critical areas aren’t overlooked. Data maps are visual representations that help organizations understand data movements across borders and within critical aspects of an organization’s data environments.
Data visualizations help companies understand the data they hold and build controls to manage any inherent risk. This information factors into the transparent processing activities disclosures made with your data subjects.
Proactiveness is a primary benefit of the data inventory and mapping process. It demonstrates to regulators that you’re not taking shortcuts to comply with regulations.
If you did miss something, a comprehensive data inventory and map will prove you genuinely take data privacy matters seriously. The process signals to regulators that you are interested in getting it right and are willing to be transparent.
Additionally, it aligns well with the data protection principles outlined in GDPR Article 5. The principles explain that personal data should be accurate and securely processed lawfully, fairly, and transparently to the data subject.
It is the controller’s responsibility to comply with GDPR and demonstrate compliance (Accountability Principle).
Conducting a data inventory is foundational for your privacy program. It can help you better respond to data access requests, improve data governance, and increase business efficiency.
How does a data inventory support GDPR Article 30 compliance?
GDPR Article 30 pertains to records of processing activities – commonly referred to as ROPA. It requires organizations to keep records and provide them to the supervisory authority upon request.
Compliance with Article 30 requires you to demonstrate all details of personal information collection, where it’s stored, shared, and used, and who is responsible for those data records. The record of processing activities must be in writing, including electronic form.
Controllers are required to record the following activities:
- The name and contact details of the controller and, where applicable, the joint controller, the controller’s representative, and the data protection officer
- The purposes of the processing
- A description of the categories of data subjects and the categories of personal data
- The categories of recipients to whom the personal data have been or will be disclosed, including recipients in third countries or international organizations
- Where applicable, transfers of personal data to a third country of an international organization, including the identification of that third country or international organization, and in the case of transfers referred to in the second subparagraph of Article 49(1), the documentation of suitable safeguards.
- Where possible, the time limits for deleting the different categories of data
- Where possible, a general description of the technical and organizational security measures is referred to in Article 32(1).
Organizations commonly perform a data inventory exercise to gather an accurate record of processing activities.
Business processes are mapped to understand how personal information is processed, what third parties have access to data, what systems are used, and what controls are in place for those systems.
The goal is to understand and demonstrate that the organization knows how personal data is processed, the third parties involved in processing activities, and the systems and controls that are working or lacking.
GDPR Article 30 compliance also requires the organization to have a legal basis for specific processing activities related to sensitive data. Strictly focusing on the data elements themselves may cause a company to overlook important elements.
As a result, companies have shifted how they observe data existing in their organization. Instead of creating static lists of IT applications, mapping business processes explains the how and why of data processing, making Article 30 reporting easier.
Getting buy-in from internal stakeholders
Building a thorough data inventory process requires effort across the organization. The best person to lead this effort is the person that will create awareness and proactively drive the process forward.
Data privacy doesn’t live with legal, risk management, information security, cybersecurity, or compliance – it needs the cooperation of all departments and the support of senior management to be efficient.
The data inventory champion should communicate internally how GDPR Article 30 compliance is essential to business and your client commitment. Today it’s often required in client contracts. Not to mention, the fines for non-compliance are rather hefty.
Benefits of data inventory for internal stakeholders
- Information Technology (IT) – Identify storage redundancies, reduce infrastructure complexity, and generate cost savings.
- Information Security – Know what data resides in each system, prioritize protection efforts, focus on the most high-risk or high-value data, establish appropriate access controls, and generate cost savings.
- Operations – Reduce redundancies and risk, improve efficiencies, and save money.
- Procurement – Identify points at which the company shares information with third-party vendors and the sensitivity of the data being shared. Support risk-based vendor management, increase efficiency in contract management, and generate cost savings.
Conducting a data inventory
Before the organization conducts a data inventory, have a vision and goal, and stick to that aspiration. What are you trying to achieve?
Depending on your organization’s size, a large amount of data could be processed and stored. To focus and gain momentum, start with the processes and areas dealing with personal data or that create high risk.
First, you need to determine if you will take a systems based approach or a business process based approach for your data inventory.
Some find it easier to give information through a process approach because people think and do their jobs from a process perspective.
The IT/systems approach
The systems approach starts with listing all databases, applications, and systems used to process or store data. The systems come first; eventually, the data flows to users or people.
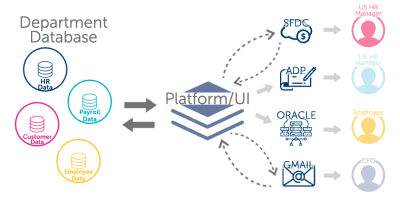
The process approach
A process approach to data inventory examines all the business processes that contain personal information. For each process, describe the data and systems that might be associated with it. Typically the data will flow appears less complicated using this method.
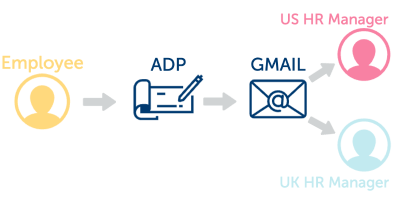
Many organizations find the process approach better encapsulates all systems than the IT approach. Most likely because it’s common for organizations to lack a complete record of systems, despite their efforts. People often download apps and use web-based applications that go unreported to IT.
To simplify this challenge, TrustArc’s AI-driven tools automate up to 80% of business process mapping. They analyze your data inventory, applicable external sources, and suggest relevant systems and workflows, and even flag gaps—all in minutes. This enhances accuracy while allowing your team to concentrate on more strategic priorities.
No matter the approach, strive to find the right balance between enough granularity to get at the complexity of data flows and understand them in a linear way, but not so granular that you’re getting the same information over and over from multiple processes.
It’s a complex job to determine. But it’s time well spent.
Four steps to conduct your data inventory
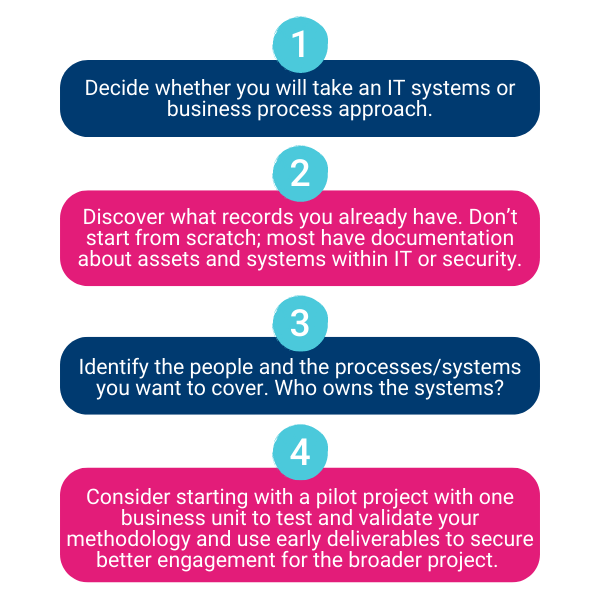
Step 1: Decide whether you will take an IT/systems or business process approach.
Step 2: Discover what records you already have. Don’t start from scratch; most have documentation about assets and systems within IT or security.
Step 3: Identify the people and the processes/systems you want to cover. Who owns the systems?
Step 4: Consider starting with a pilot project with one business unit to test and validate your methodology and use early deliverables to secure better engagement for the broader project.
Organizations new to this process often start with a data inventory spreadsheet. Information is collected within each process or system area to document how the data flows. This information creates a data map to visualize who owns the systems, where the data comes from, who the data subjects are, and whether or not the data is encrypted.
Business process mapping can be complex in larger organizations. Using a data mapping tool to visualize the data as it moves provides much-needed clarity compared to a spreadsheet.
Data inventories and visual maps are used together to capture the total picture in an easy, detailed format. And speaking of the total picture, don’t forget your suppliers and third-party vendors.
Addressing third party vendors
Know which suppliers and third-party vendors are either in the EU or may handle EU personal data. This is especially important for GDPR Article 30 compliance but also for compliance with other data privacy laws.
After you’ve created an inventory of vendors, classify the vendors. Which third parties have access to critical or sensitive information?
Address each vendor with a customized policy and procedure document that includes vendor vetting, ongoing reviews and audits, and end-of-relationship activities. Although end-of-relationship activities are often overlooked, be sure to include off-boarding, deletion of data, or returning data and how you will attest to that.
As you continue to manage your third-party risk, include data privacy in your onboarding process for new suppliers and contractors.
The onboarding process should include:
- Identifying the types of information they will be handling/processing
- Considering whether or not they have logical or physical access
- Getting an impression of inherent risk and a window into security and privacy practices.
Ensure that issues not up to your standards are remediated before finalizing the relationship.
Ongoing maintenance of data inventory for GDPR Article 30 compliance
Compliance with Article 30 requires more than checking off a to-do list. A data inventory is a living, breathing document. It needs to be maintained through acquisitions, mergers, and technological changes.
Keeping your data inventory up to date is just as important as building it. Once you’ve established your data inventory, identify tools and methodologies that can maintain and scale the process.
Use the data inventory as a foundation for ongoing GDPR compliance program
GDPR compliance doesn’t end with Article 30. But it’s a great place to start when building an ongoing data privacy compliance program. Once you’ve established this foundation, consider these next steps.
- Identify inherent risk and complete DPIAs as required under Article 35.
- If you have a sub-processor or vendor contracts, do that due diligence, and ensure vendors uphold the same principles in privacy that your organization holds.
- Train employees continuously on data inventory change management.
- Share processes with cross-functional teams for broader organizational benefit.
- Leverage the data inventory for the next phase in your compliance mission; implement appropriate technical controls.
Test your data inventory process
After you’ve completed the data inventory, test your process to ensure it works. One way to test your process is by conducting a simulated data breach with team members in their respective roles.
The team will respond to the simulated breach by identifying the data breached, where it resides, and which processes were affected. These requirements will identify whether the data inventory is accurate.
For example, can your team pinpoint every vendor that had access to that data? If not, there is likely a gap in your data inventory process.
Essential Guide to the GDPR
Practical steps to manage the EU General Data Protection Regulation, including a compliance roadmap for implementation.
Download the guideData Mapping & Risk Manager
Automate data mapping and ROPAs to generate data flow maps for compliance.
Find out more




