GDPR compliance is a challenge for organizations of all sizes
The EU’s General Data Protection Regulation (GDPR) has been enforceable since 25 May 2018. In recent years, we’ve seen an increase in prosecutions following large data breaches and other non-compliance activities.
Some of the biggest technology companies in the world have already been charged in several jurisdictions with non-compliance to GDPR, including:
- Amazon (fined US$866 million in July 2021)
- WhatsApp (fined US$255 million in August 2021)
- Google Ireland (fined US$102 million in January 2022) and Google LLC (fined US$56.6 million in 2019 and another US$68 million in January 2022)
- Facebook (fined US$68 million in January 2022).
Understandably, these tech giants are big targets for GDPR-compliance scrutiny, though they also have huge resources for managing their response and recovery following a breach.
Still, all organizations, regardless of size, find it challenging to prove GDPR and other data privacy law compliance.
Many have already invested huge amounts of time and resources in designing and implementing GDPR compliance programs.
Documenting a data privacy program often generates hundreds or thousands of pages of information related to internal data security and privacy policies and processes. And reports on implementation of these policies across the organization including Article 30 records and Article 35 data protection impact assessment (DPIA) reports.
Therefore, demonstrating data privacy compliance to internal and external stakeholders can be equally challenging.
Most stakeholders will want an overview of your organization’s cybersecurity policies to confirm the essential rules for compliance are in place.
Though, more importantly, they will want some proof of how these policies are carried out in day-to-day business practices – and of course they will want to know about how any incidents are managed.
Adding traceability to the classic ‘CIA triad’ foundations
Before GDPR, cybersecurity policies were often designed with the ‘CIA triad’, a model with three key foundations:
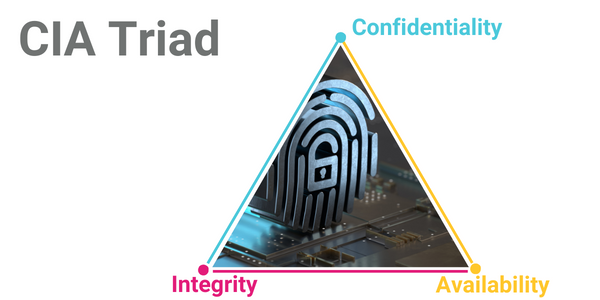
Confidentiality
Securing private information and preventing unauthorized access. Privacy rules for managing and protecting sensitive and/or secret information are built on this foundation.
They include procedures for controlling access, such as multi-factor authentication, and processes for managing and updating permissions.
Integrity
Keeping data intact (unchanged) throughout its lifecycle so it is truly accurate and trustworthy.
Data processing and access rules to ensure information cannot be changed or compromised by unauthorized parties are built on this foundation.
They include practices for keeping employees and stakeholders up to date with data regulations, safeguards to prevent human error, and policies for integrity controls (versions, access, security) and backups/recovery.
Availability
Making information reliably and quickly available to authorized parties.
Storage rules, including maintenance policies for hardware and other technologies used to manage and display data, are built on this foundation.
They include policies for business continuity, including rules for how systems are monitored, updated and recovered (redundancy and failover).
(Note: the CIA triad model is sometimes referred to as the AIC triad so that people don’t mistake it as a reference to the US Central Intelligence Agency.)
Since the introduction of the GDPR many cybersecurity professionals have also added another foundation:
Traceability
Maintaining records of all data processing activities, which must be readily available for audit (Article 30 of the GDPR).
Recording keeping rules to ensure information is accurate and up to date are built on this foundation.
- These records must contain information on the responsible parties (controllers, processors and data protection officers);
- purposes of processing;
- categories of data subjects and the categories of personal data;
- categories of recipients of personal data;
- planned time limits for erasure of different data categories;
- and descriptions of technical and organizational security measures.
Traceability is an important consideration for all organizations under GDPR as accurate and current records are essential for any compliance audit.
Without these records, it can be very difficult to prove adherence to the core principle of GDPR that ‘the protection of natural persons in relation to the processing of personal data is a fundamental right’.
Giving individuals in the EU more rights to access, delete and/or control the use of data relating to them.
Choosing a reliable approach to GDPR compliance
Some companies are pursuing an ISO / IEC 27001 certification (which is designed to map against the ‘CIA triad’) to show GDPR compliance.
However, the ISO 27001 security standard represents only a partial fit for coverage against the requirements of the GDPR.
There are several other avenues organizations might consider:
- Codes of conduct and/or certifications – although the GDPR text refers to opportunities for these avenues, to date no official GDPR codes of conduct or certifications have been issued.
- Some organizations have become members of the General Assembly of the EU Cloud Code of Conduct.
- EU-US Privacy Shield Verification or APEC Cross-Border Privacy Rules (CBPR) certification – these certifications share some significant overlaps on privacy objectives and controls, but they do not represent complete solutions.
- However, they can help lay the foundation for a company to later qualify for the official GDPR certification when it becomes available.
- External validation – in the absence of an official GDPR certification, organizations looking for efficient ways to benchmark and report on their compliance are engaging independent experts to give weight to their efforts now.
- These external validations can help show customers, business partners and other stakeholders how an organization is meeting GDPR requirements. TrustArc GDPR Validation is designed to meet that need.
TrustArc GDPR Validation
The TrustArc GDPR Validation requirements are mapped to each applicable Article of the GDPR, Article 29 Working Party / EDPB guidelines, ISO 27001 and other relevant standards.
Organizations choosing our GDPR Validation can demonstrate their GDPR compliance efforts and status using intelligent technology-powered assessments, managed services and independent compliance validation.
The solution is powered by the Assessment Manager module of the TrustArc Platform to simplify multiple processes including:
- Managing assessments
- Identifying policy and implementation gaps
- Reviewing remediation recommendations
- Assigning tasks, recording the audit trail of changes and generating reports.
Get support from TrustArc GDPR Validation to independently validate GDPR compliance with an assessment of your organization’s privacy program and/or assessment of specific processes or technologies.
Guide to Addressing GDPR Consent Requirements
Understand the impact of the GDPR consent requirements on business operations.
Download the ebookEssential Guide to the GDPR
Practical steps to manage the EU General Data Protection Regulation, including a compliance roadmap for implementation.
Download the guide




